Reaver Wps For Mac
Reaver mac of the host system. Reaver (reaver-wps-fork-t6x) One of the most popular adapters that use the Atheros chipset is from Alfa. The problem is that it became too much popular, thus some chineses started to faking it. This finding was shocking for me. To verify if what you bought was counterfeited or not, you can ask Alfa. Reaver is a tool to brute-force the WPS of a WIFi router. PixeWPS is a new tool to brute-force the exchanging keys during a WPS transaction. First, let’s get to know what is WPS. WPS is Wifi Protected Setup designed to quickly & easily authenticate a client to an AP mainly aimed for home users. Reaver is a tool to brute-force the WPS of a WIFi router. PixeWPS is a new tool to brute-force the exchanging keys during a WPS transaction. First, let’s get to know what is WPS. WPS is Wifi Protected Setup designed to quickly & easily authenticate a client to an AP mainly aimed for home users. Jan 06, 2016 reaver windows free download. Xiaopan OS Xiaopan OS is an easy to use software package for beginners and experts that includes a number of ad.
- Wps For Mac Download
- Reaver Wps For Mac Installer
- Reaver Wps For Mac Windows 10
- Reaver Wps For Mac Download
- Reaver Wps For Mac Windows 10
- Reaver Wps For Mac Os
- Wps
Introduction
Reaver is an open-source tool for performing brute force attack against Wifi Protected Setup (WPS) registrar PINs in order to recover WPA/WPA2 passphrases. This tool has been designed to be a robust and practical and has been tested against a wide variety of access points and WPS implementations.
Wifi Protected Setup (WPS)
Reaver: Brute force attack against WiFi Protected Setup
The original Reaver performs a brute force attack against the AP, attempting every possible combination in order to guess the AP’s 8 digit pin number. Depending on the target’s Access Point (AP), Reaver will recover the AP’s plain text WPA / WPA2 passphrase in 4-10 hours, on average. But If you are using offline attack and the AP is vulnerable, it may take only a few seconds/minutes.
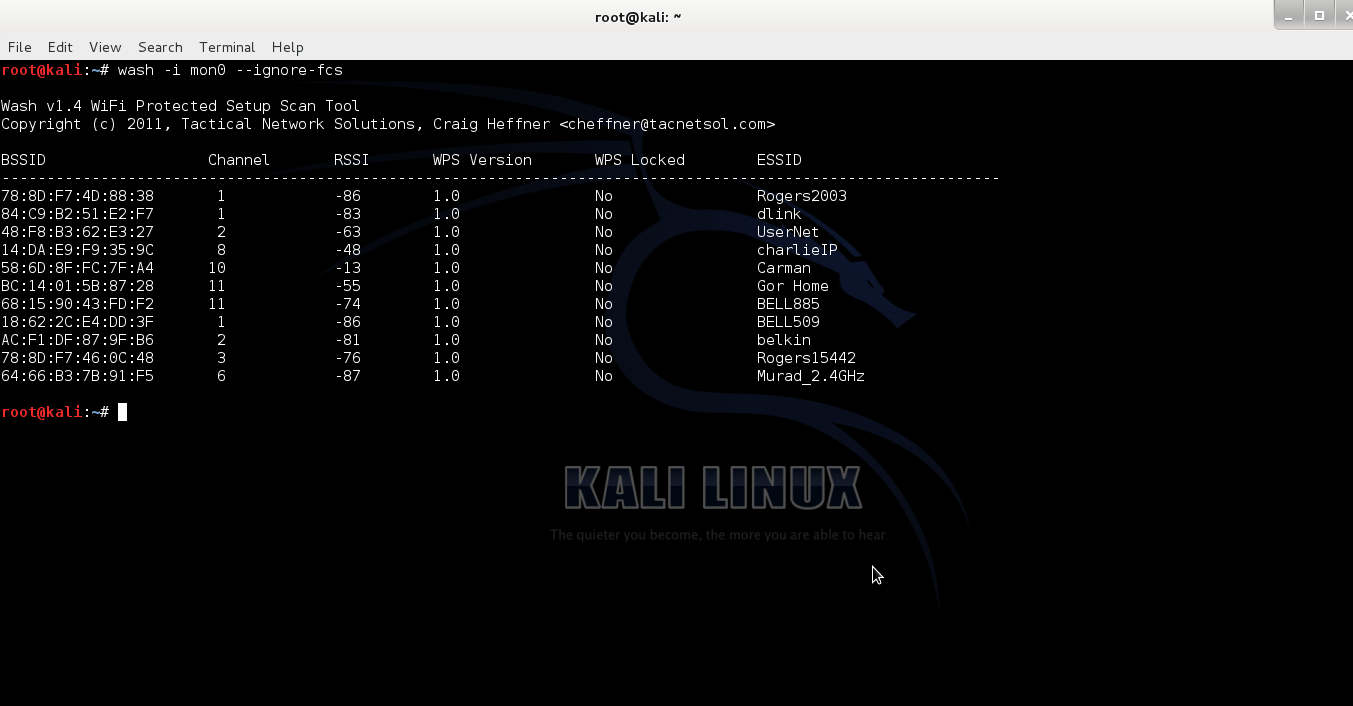
reaver 1.0) was created by Craig Heffner in 2011.You can find the original Reaver, version 1.0 to 1.4, in google code archives. From version 1.4, reaver-wps comes with a simple and fast WPS scanner – wash.
Supported wireless drivers:
- ath9k, rtl8187, carl19170, ipw2000, rt2800pci, rt73usb
- partially supported: ath5k, iwlagn, rtl2800usb, b43
reaver-wps-fork-t6x
Reaver-wps-fork-t6x version 1.6.x is a community forked version of the original Reaver, which includes various bug fixes, new features and additional attack method – offline Pixie Dust attack. Since this fork supports Pixie Dust attack, you’ll be able to preform it against modern routers.
Features:
- Support for the offline Pixie Dust attack.
- Improved argument -p with an Arbitrary String (
-p, --pin=<wps pin>) - New wash: Compatibility with all supported WiFi chips, wash now displays the correct signal level with all the (supported) WiFi chips.
- Power to the user with the pipe compatibility: You can now modify “on the fly” wash’s stdout with pipe compatibility.
- …
Requirements
Build-time dependencies:
Wps For Mac Download
libpcap-devbuild-essential
Runtime-time dependencies:
pixiewps(optional, required for Pixie Dust attack)aircrack-ng(optional, though recommended)
To install dependencies, run the following:
Install
Reaver-wps comes preinstalled in Kali Linux & BlackArch Linux. It can be installed on any other Linux via source code.
First of all, clone it from the github:
or download:
Then locate the shell:
and compile:
Now you can install it with the following:
Basic Reaver Usage
Use -h to list available options:
New Options/Features:
-K or -Z // --pixie-dust: perform the offline attack, Pixie Dust (pixiewps), by automatically passing thePKE,PKR,E-Hash1,E-Hash2,E-NonceandAuthkeyvariables.-p with arbitrary string // --pin=: can be used against Access Points that do not follow the WPS checksum on the last digit of the PIN.
-S) option. User will have to execute Reaver with the cracked PIN (option -p) to get the WPA pass-phrase.Example:
To use reaver you’ll only need the interface name and the BSSID of the target AP. If you want to get more detailed information about the attack as it progresses, run the reaver in the verbose mode.
Basic Wash Usage
You can also type -h to list all available wash options:
New Options/Features:
-a // --all: this option will list all access points, including those without WPS enabled.-j // --json: the extended WPS information (serial, model…) from the AP probe answer will be printed in the terminal (in json format).
Reaver Wps For Mac Installer
Example:
To scan for networks you can use option --scan, just run:
Reaver Description
Reaver has been designed to be a robust and practical attack against Wi-Fi Protected Setup (WPS) registrar PINs in order to recover WPA/WPA2 passphrases. It has been tested against a wide variety of access points and WPS implementations.
The original Reaver implements a online brute force attack against, as described in http://sviehb.files.wordpress.com/2011/12/viehboeck_wps.pdf. reaver-wps-fork-t6x is a community forked version, which has included various bug fixes and additional attack method (the offline Pixie Dust attack).
Depending on the target's Access Point (AP), to recover the plain text WPA/WPA2 passphrase the average amount of time for the transitional online brute force method is between 4-10 hours. In practice, it will generally take half this time to guess the correct WPS pin and recover the passphrase. When using the offline attack, if the AP is vulnerable, it may take only a matter of seconds to minutes.
Homepage: https://github.com/t6x/reaver-wps-fork-t6x
Author: Tactical Network Solutions, Craig Heffner, t6_x, DataHead, Soxrok2212
License: GPLv2
Reaver Help
-K or -Z // --pixie-dust
The -K and -Z option perform the offline attack, Pixie Dust (pixiewps), by automatically passing the PKE, PKR, E-Hash1, E-Hash2, E-Nonce and Authkey variables. pixiewps will then try to attack Ralink, Broadcom and Realtek detected chipset.Special note: If you are attacking a Realtek AP, do NOT use small DH Keys (-S) option. User will have to execute reaver with the cracked PIN (option -p) to get the WPA pass-phrase. This is a temporary solution and an option to do a full attack will be implemented soon
-p with arbitrary string // --pin=
It can be used against Access Points that do not follow the WPS checksum on the last digit of the PIN.
See also: Introducing a new way to crack WPS: Option p with an Arbitrary String
Reaver Wps For Mac Windows 10
Reaver Options
Usually, the only required arguments to Reaver are the interface name and the BSSID of the target AP:
It is suggested that you run Reaver in verbose mode in order to get more detailed information about the attack as it progresses:
The channel and SSID (provided that the SSID is not cloaked) of the target AP will be automatically identified by Reaver, unless explicitly specified on the command line:
Since version 1.3, Reaver implements the small DH key optimization as suggested by Stefan which can speed up the attack speed:
By default, if the AP switches channels, Reaver will also change its channel accordingly. However, this feature may be disabled by fixing the interface's channel:
When spoofing your MAC address, you must set the desired address to spoof using the ifconfig utility, and additionally tell Reaver what the spoofed address is:
The default receive timeout period is 5 seconds. This timeout period can be set manually if necessary (minimum timeout period is 1 second):
Reaver Wps For Mac Download
The default delay period between pin attempts is 1 second. This value can be increased or decreased to any non-negative integer value. A value of zero means no delay:
Some APs will temporarily lock their WPS state, typically for five minutes or less, when 'suspicious' activity is detected. By default when a locked state is detected, Reaver will check the state every 315 seconds (5 minutes and 15 seconds) and not continue brute forcing pins until the WPS state is unlocked.
This check can be increased or decreased to any non-negative integer value:
The default timeout period for receiving the M5 and M7 WPS response messages is .1 seconds. This timeout period can be set manually if necessary (max timeout period is 1 second):
Some poor WPS implementations will drop a connection on the floor when an invalid pin is supplied instead of responding with a NACK message as the specs dictate. To account for this, if an M5/M7 timeout is reached, it is treated the same as a NACK by default. However, if it is known that the target AP sends NACKS (most do), this feature can be disabled to ensure better reliability. This option is largely useless as Reaver will auto-detect if an AP properly responds with NACKs or not:
Reaver Wps For Mac Windows 10
While most APs don't care, sending an EAP FAIL message to close out a WPS session is sometimes necessary.

By default this feature is disabled, but can be enabled for those APs that need it:
When 10 consecutive unexpected WPS errors are encountered, a warning message will be displayed. Since this may be a sign that the AP is rate limiting pin attempts or simply being overloaded, a sleep can be put in place that will occur whenever these warning messages appear:
Reaver Usage Example
How to install Reaver
The program is pre-installed on Kali Linux.
Reaver Wps For Mac Os
Installation on Linux (Debian, Mint, Ubuntu)
First, install PixieWPS. Next:
Reaver Screenshots
Reaver Tutorials
Related tools
Wps
- airgeddon (100%)
- PixieWPS (95.9%)
- Wash (84.5%)
- Router Scan (77.3%)
- WiFi-autopwner (77.3%)
- Aircrack-ng (Tool) (RANDOM - 56.8%)
